The beginning of a new year inevitably comes with summarizing the previous one. While yearly statistics mainly relate to achievements and positive nutshells, the time has come to face more frustrating conclusions. In this case – the vexing data by Chainalysis, indicates the overwhelming rise of approval phishing volume over the last two years.
To heed cryptocurrency security, we’ll dive into the most popular approval phishing tactics and disclose the research by Chainalysis from A to Z.
What Is Approval Phishing
“Approval phishing” (sometimes referred to as “ice phishing”) is a long-existent scamming tactic, which yet has almost nothing to do with traditional crypto scams.
While typical phishing envisages tricking a victim into sending a cryptocurrency through a phony investment opportunity or by impersonating somebody else, approval phishing is much more ornate.
By contrast, an ice phisher tricks a victim into signing a malicious blockchain transaction that opens access to the victim’s wallet so the attacker can steal all the assets. In such cases, victims are often lured onto a phishing website designed to mimic real crypto services.
According to BeInCrypto, some approval phishing victims lost tens of millions of dollars. Meanwhile, Chainalysis cites more common data of $347 million suspected to be stolen through ice phishing.
How Approval Phishers Trick Their Victims
Approval phishing scams are carried out by a typical pattern that includes the following structure:
- The victim address signs transactions, approving the second address to spend its funds
- The second address (approved spender address) executes the transaction to move funds to a new destination address.
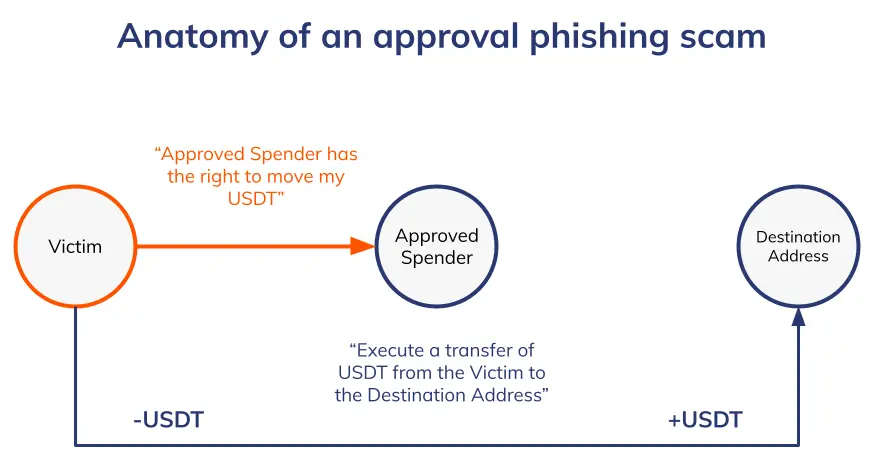
Anatomy of an approval phishing scam. Source: Chainalysis
Crucially, according to Chainalysis, the decentralized apps (dApps) on smart contract-enable blockchains are the most preferable area for ice phishers. The reason behind this is their on-chain structure.
A vast majority of dApps require users to sign approval transactions, giving the apps’ smart contract permission to move funds held by the user’s address.
Such approvals are generally safe, seeing that smart contracts’ structure requires a direct confirmation by the user, and user addresses initiate the transactions through dApps.
However, approval phishers can take advantage of the fact that crypto users are simply used to signing approval transactions. The trick lies in the permissions given and the trustworthiness of the party receiving this permission.
How Abundant Approval Phishing Is
Within the research, Chainalysis identified at least 1,013 addresses involved in ice phishing. The calculations revealed that the victims have lost approximately $1 billion to approval phishing scams since May 2021.
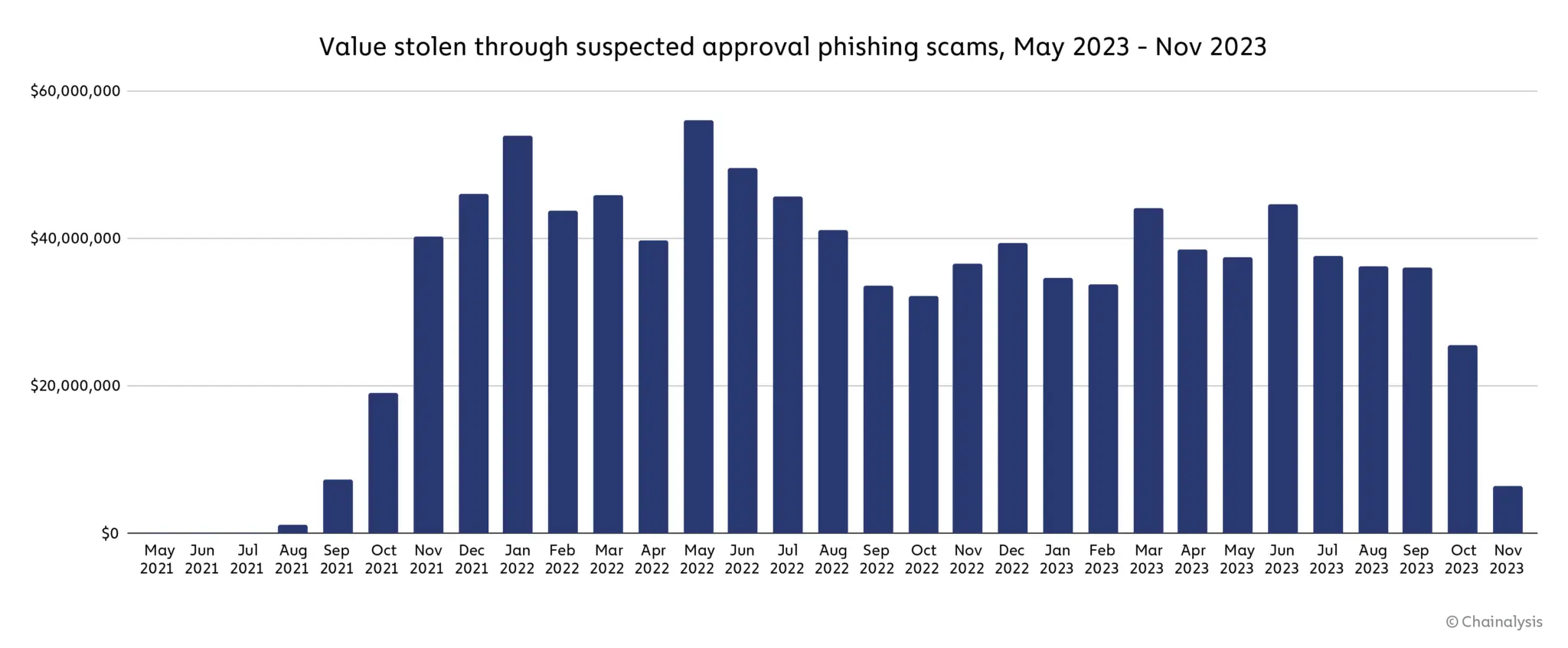
Value stolen through suspected approval phishing scams, May 2021 – November 2023. Source: Chainalysis
Significantly, the peak of approval phishing cases was noted in May 2022. That year turned out to be the most rewarding for scammers, as $516.6 million equivalent of crypto was lost by the victims of ice phishing versus just $374.6 million in 2023.
However, approval phishing can not be named traditionally abundant, seeing that the vast majority of scam cases are driven by a few highly successful actors.
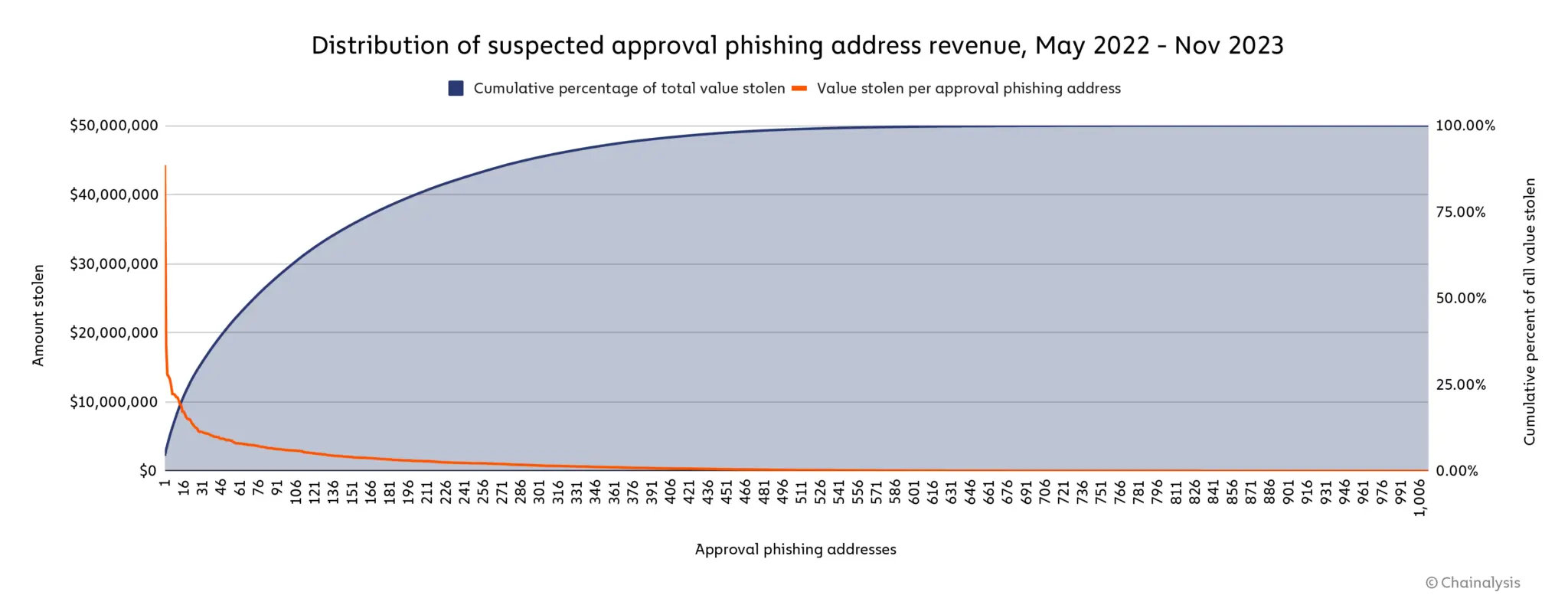
Distribution of suspected approval phishing address revenue, May 2022 – November 2023. Source: Chainalysis
Namely, the most successful ice phishing address likely stole $44.3 million from thousands of victims’ addresses, representing 4.4% of the total estimated phishing volume. At the same time, 15.9% of the stolen value was transferred to only the ten largest approved phishing addresses, while half of the funds were tracked down to 73 accounts.
Closing Remarks: How to Secure Yourself from Approval Phishing Scams
By and large, the approval phishing problem can be solved in various ways – from proper security education to employing pattern recognition tactics.
However, to mitigate the risks more effectively, it is essential to know that the stolen funds are moved from destination addresses to consolidation addresses, from which they are spread between the actors. This means, any scammer’s “reward” will inevitably end up in a certain centralized exchange (CEX) address on its way to cashout.
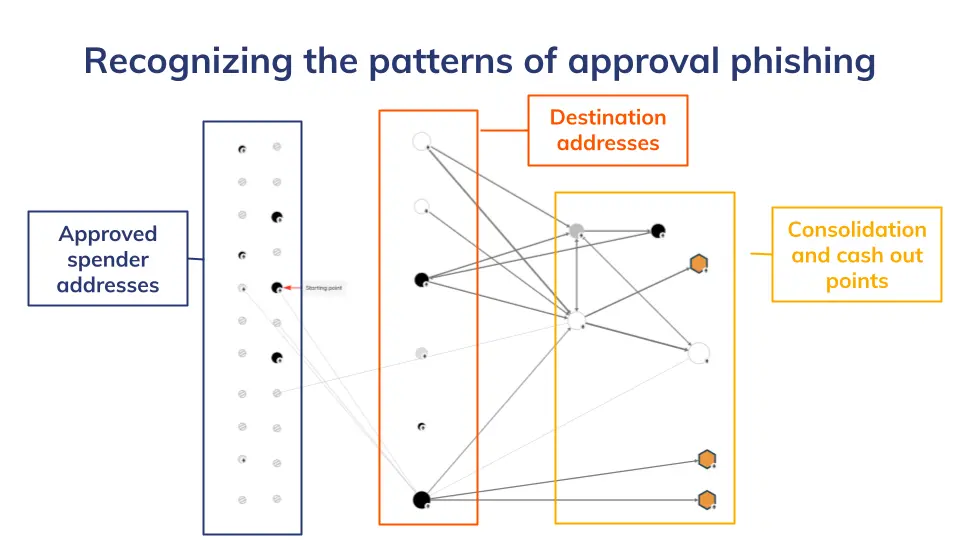
Various patterns of approval phishing. Source: Chainalysis
Hence, the basic rule in avoiding approval phishing scams is choosing the exchange with cutting-edge security and decent AML-policy compliances. Given this, such CEXs operate with more precise suspicious activity monitoring. The leaders in these terms are Crypto.com, Kraken, WhiteBIT, Binance, and Coinbase.
Still, the precautions remain the essence. Educate yourself, monitor your transactions with proper attention, and do not hesitate to contact support if your funds are stolen.
Remember: until the industry comes up with more complex solutions, the primary responsibility for your funds’ safety against ice phishing lies on you. Trade SAFU!
>Free Tool: Use our simple crypto profit calculator to calculate your potential profits and returns on your cryptocurrency investments.<<<
Read more:
