Decentralized finance (DeFi) protocol, Curve Finance reportedly recovers about $5.4M of stolen funds through an ethical hacker. The white hat hacker managed to retrieve 2,879 ETH and returned it to the decentralized exchange after its recent attack. The latest update was reported on Twitter by Peckshield Alert.
#PeckShieldAlert c0ffeebabe.eth has returned 2,879 $ETH (~$5.4m) to #Curve deployer https://t.co/33BJLaq12A pic.twitter.com/2Jq0JOsrhV
— PeckShieldAlert (@PeckShieldAlert) July 31, 2023
On July 30, Curve Finance experienced exploits on several stablepools which were caused by a vulnerability in reentrancy locks on several versions of the Vyper programming language.
At the time, Curve Finance’s losses are estimated to be over $47 million. According to Vyper, some of its versions including 0.2.15, 0.2.16, and 0.3.0 are vulnerable to malfunctioning reentrancy locks.
PSA: Vyper versions 0.2.15, 0.2.16 and 0.3.0 are vulnerable to malfunctioning reentrancy locks. The investigation is ongoing but any project relying on these versions should immediately reach out to us.
— Vyper (@vyperlang) July 30, 2023
Vyper vulnerability further exposed the DeFi ecosystem to a stress test as other decentralized finance protocols using the vulnerable versions were also exploited. Some of the stolen assets were retrieved that day by the ethical hacker, who then gave them back to Curve Finance.
To secure over 3,000 ETH, an MEV bot operator with the identity “c0ffeebabe.eth” utilized a front-running bot against a hostile hacker. The funds were subsequently sent back to the Curve deployer address, which appears to be the correct custodian.
Read Also: SEC Asked Coinbase to Delist Every Asset Other Than Bitcoin: XRP Lawyer Reacts
Scam amid the chaos
Meanwhile, fake Twitter accounts impersonating Curve Finance are promoting a fake refund campaign which appears to be a form of a phishing scam. The scam targets victims of the recent hack.
When properly observed, the impersonating account has an “L” before “Curve Finance” on its Twitter username which might not be very visible to users if not properly checked.
According to the scam promo, there is an “emergency CRV distribution” to all users who have interacted with Curve Finance and its affiliates.
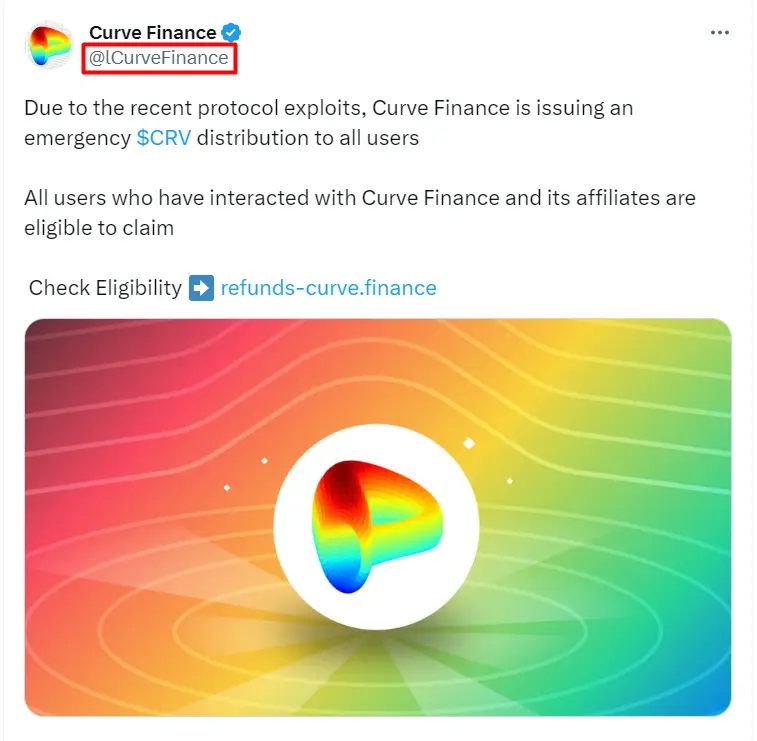
Fake curve finance account. Source: Twitter
In the meantime, the Vyper vulnerability has also led to copycat attacks against BNB Smart Chain. Data from BlockSec – a Blockchain security company, shows that through three vulnerabilities, almost $73,000 was lost.
Also, the Securities and Exchange Commission has set out new rules regarding cyber attacks involving public companies in the United States. Per the new rule, companies affected are to disclose the attack four days after it has been considered as “material.”


